 Understanding Commitment Control Security
Understanding Commitment Control SecurityThis chapter provides an overview of setting up security for Commitment Control and describes how to:
Set up security fields.
Set up security events.
Set up security rules.
Assign security rules to user IDs, permission lists, and dynamic views.
Run the Commitment Control Security process (KSEC_FLAT) and Commitment Control Security report (GLC8572).
Set up PS/nVision reporting security.
 Understanding Commitment Control Security
Understanding Commitment Control SecurityCommitment Control security augments the security used by your PeopleSoft applications, enabling you to secure the Commitment Control functions, such as creating or modifying budgets or overriding exceptions, that a user may perform on ChartField combinations for which you have established control budgets.
To set up Commitment Control security, you define a series of security rules that enable particular commitment control functions for particular budgets. You then apply those security rules to user IDs, permission lists, or dynamic views consisting of user IDs and associated ChartFields.
In this section, we discuss the following:
Security set up order.
Security events.
Security rules.
Security rule assignment.

 Security Set up Order
Security Set up OrderUse the following order for setting up security for Commitment Control:
Enable standard PeopleSoft application security. Define users, roles, and permission lists.
Note. Coordination of overall system security options and commitment control security is important. For example, if you select options
on the Security Options page by user ID and if you select only the Business Unit check box and not the Ledger check box, the
user is not able to select any ledger group for budget journals. Instead the system returns the message "No matching values
were found" and the user cannot select ledger groups.
In other words, when the Security Options page has User ID Level Security checked, for any user who wants to access Ledger
Group, the Ledger check box for Secured Fields must be checked and Ledger by User ID must be appropriately setup.
Security field setup comes predefined. We recommend that you not edit any of the fields on this page unless you are configuring (making changes, such as adding deleting, activating, inactivating, or renaming) Commitment Control ChartFields.
If you are configuring ChartFields, define the ChartFields that you want to secure on the Security Field Setup page. You can establish security for any ChartField that you define as a key ChartField in the control budget definition, as well as Budget Period, Ledger Group, and Ledger.
Select the events that you want to secure on the Security Events page.
Commitment Control predefines the seven events that can trigger security: Budget Entry or Adjustment, Budget Transfers, Bypass Budget, Budget Override, Budget Date Override, Workflow Notification, and Budget Inquiry.
The default security setting for these events is inactive.
Note. It is useful to know which events you want to secure before you proceed with security setup, however, it might be helpful to defer activating security events until just before running the security build process. The security build process builds the security records only for events that are activated. Deferring activation enables you to verify that the security rules you are building correctly enforce the security events, and it insures that you are not hampered by security being activated during setup or until you are ready for security to be applied.
Define security rules for these events in the Rule Definitions component.
Security rules apply event security to the ChartField combinations (budgets) that you want to secure.
Assign security rules to individual user IDs and permission lists to tell the system which events a user has the authority to conduct for specific budgets. You can also apply security rules dynamically, using a pre-defined record that contains the user IDs and the ChartField or ChartFileds defined in a dynamic rule group. Use the Associate Rules to User ID, Assoc Rules to Permission List, or Attach Dynamic Rules pages.
Run the Commitment Control Security process (KSEC_FLAT), also known as the security flattening process, from the Request Build page.
This process uses security rules and assignments to populate the tables that the system uses to check security authority during transaction entry. This Application Engine process must be run before security rules and assignments become effective.
You can Run the Commitment Control Security report (GLC8572) to view the results of the Commitment Control Security process.
The system uses these security settings to enforce security for Commitment Control across all applications in your installation. Any event that requires security processing initiates a call to the security function on a predetermined trigger, such as entering or saving a page. The system does not process any events that fail the security rule for the user ID.
See Also
Key ChartFields and Translation Trees
Enterprise PeopleTools 8.46 PeopleBook: PeopleSoft Security

 Security Events
Security EventsCommitment Control uses security events to enable you to specify the budgetary functions, or events, on which the system enforces security. There are seven event types for which you can enable security:
Budget Entry or Adjustment
Budget Transfer
Budget Override
Budget Date Override
Bypass Budget
Workflow Notification
Budget Inquire
You enable security separately for each event on the Security Events page. This enables you to decide whether to implement security across all control-budgeting functions (events) or a limited set of functions. For example, you may want to enable security for budget journal entry and adjustments to limit this activity to a small set of users, but not enable security for inquiring on existing budgets so that all users can check on the status of a budgeted amount.
The following table shows how each security event restricts access to Commitment Control functions when you activate it. The table also provides links to detailed discussions of the functions themselves:
|
Security Event |
Functions |
Further Discussion |
|
Enables you to restrict budget journal (budget amount) entry to a limited set of users. You can also restrict users to specific budgets using ChartField values. |
See Understanding Entering and Posting Commitment Control Budget Journals. |
|
|
Enables you to restrict or add constraints to the ability of the user to transfer funds from one budget to another. |
See Understanding Entering and Posting Commitment Control Budget Journals. |
|
|
Enables you to restrict or add constraints to the ability of the user to override budget checking. Budget- checking override enables users to override budget checking exceptions for a new transaction or to pass a transaction that has failed budget checking. Note. If Commitment Control security is active for the budget override event, the commitment control security rules will supersede the override setting for the Source Transaction Definition . The override setting on the Source Transaction Definition is taken into consideration by the system only when the override event is inactive within Commitment Control security. Note. Override at the transaction level, or header level, as for a complete override of a journal entry, can be done by a super user only. Overrides at the individual budget level for source transactions can be established for other than a super user rule. |
||
|
The notification feature in Commitment Control enables users to be notified by workflow when budget exceptions occur or when a specified percentage of the budget has been used (Early Warning notification). Activating the Workflow Notification security event enables you to limit the budgets that a user can specify for notification. |
||
|
Enables you to limit the users who can view control budgets. |
||
|
Enables you to limit the users who can create a General Ledger journal that bypasses budget checking entirely (as opposed to overriding a budget checking exception). A journal that bypasses budget checking never updates the control budget ledger. This function is reserved for occasions such as when a user needs to correct a suspense journal that was generated from within a source application like Purchasing and whose accounting entries have already been budget-checked. Users may also want to bypass budget checking for journals that are created in the allocation process, when, for example:
|
||
|
Enables you to limit the users who can override the system-defined budget date on a source transaction. Note. You can attach this event only to a Super User security rule. |
See Budget Processor. |

 Security Rules
Security RulesSecurity rules enable you to establish which security events can be performed on which budgets and which transactions independent of any specific user until such time as you apply the rules to a user or users. For example, you can create one security rule to enable budget entry, transfers, notification, and inquiry for a budget (or group of budgets) and create a different security rule that enables only inquiry for the same budget (or budget group). After you define your security rules, you can assign these rules to a specific user ID or all the users and roles assigned to a permission list. You can also use a dynamic rule group, which uses a SQL view that joins user IDs with ChartField values to dynamically assign users access to budgets with particular ChartField values.
The following rules govern how Commitment Control applies security rules to user IDs and permission lists:
For events that do not require a Super User rule, you can create security rules that allow access to the budgets you specify for the security events you specify. You can also create security rules that disallow such access.
Note. A Super User rule is required to perform budget override, date override, and bypass at the transaction level.
When you assign a user to a security rule that allows access, the system denies the user access to any budgets and active security events that are not specified in that security rule, unless that user is assigned to another security rule that does allow access to budgets and security events not specified in the first security rule.
When you assign a user to a security rule that disallows access, the system denies the user access to the budgets and active security events you specify and gives the user access to all other budgets for those security events, unless that user is assigned to another security rule that disallows access to those unspecified budgets.
The choice between allow and disallow can save you time and effort when defining security rules. When you want to allow access to only a few budgets, use the allow attribute to specify them. When you want to allow access to all but a handful of budgets, use the disallow attribute to specify those that you want to deny access to instead of entering rows and rows of allowed budgets.
Note. All users automatically have access to inactive security events for all budgets, regardless of the security rules you establish.
You can create security rules defined solely for Super Users.
You can assign multiple security rules to a single user—that is, a user may have one set of security rights for one group of budgets and a different set of security rights for another group of budgets.
If you grant a user multiple security rules, and the security rules provide conflicting security access, the security rules that disallow access take precedence.
You must set up and assign security rules for users to provide access to any security event that is active. If no security rules for a particular security event are assigned to a user, then that user has no access to that security event for any budget.
The following example provides a simplified illustration of how you can use security rules to limit a user’s access to a specific set of events for a set of budgets.
Table 1: Associating Security Rules with Security Events:
|
Sec Rule |
Bdgt (CF combo) |
ENT_ADJT |
Transfer |
NOTIFY |
INQUIRE |
Override |
BUDG_DT |
BYPASS |
|
A |
Budget #1: Account 10000, DeptID 35000 |
Y |
N |
Y |
Y |
N |
N |
N |
|
B |
Budget #2: Account 10015, DeptID 35000 |
N |
N |
Y |
Y |
N |
N |
N |
|
C |
All Budgets |
N |
N |
N |
Y |
N |
N |
N |
Table 2: Associating User IDs with Security Rules:
|
User ID |
User |
Security Rules |
|
TJON |
Jones,Tammy |
A, B |
|
RSMI |
Smith,Roger |
B |
|
HBRO |
Brown,Harry |
C |
User Tammy Jones is associated with security rules A and B. According to security rule A, Ms. Jones has the security to perform the following events on budget #1: entering and adjusting, inquiring, and receiving notifications about exceptions. Security rule B enables her to inquire on and be notified of exceptions for Budget #2.
User Roger Smith, also associated with security rule B, can be notified whenever an exception for Budget #2 occurs and can inquire on budgetary information. However, unlike Tammy Jones, Mr. Smith cannot perform any events for Budget #1.
User Harry Brown is a Junior Financial Analyst in the corporate group. Security rule C lets him inquire on the budgetary information for all budgets, but he cannot perform any substantive actions on these budgets.
You can define security rules for specific budgets and for a range or group of budgets. Instead of specifying each individual ChartField combination that you want to include within a security rule, you can specify ranges of budgets by entering ranges of ChartField values.
There are three parameters you can use to enter ranges of ChartFields:
Range: enter the first and last ChartField value in a range. If you enter account 10000 as the start value and 20000 as the end value, for example, you include all budgets with accounts 10000 through 20000 that meet the other ChartField value criteria in the ChartField combination.
Wild Card: enter a wildcard (%). For example, if you enter department 14%, you include all budgets with departments beginning with 14 that meet the other ChartField value criteria in the ChartField combination. If you enter % alone, you include budgets for all departments that meet the other ChartField value criteria in the ChartField combination.
Tree: enter a translation tree and node to include budgets for that node and all the ChartField values that are children of that node (and which meet the other ChartField value criteria in the ChartField combination). Usually you can use the key ChartField translation trees you set up for control budget definitions.
Note. You use Explicit when you want to select a single ChartField value, which you enter in the Start field.
See Key ChartFields and Translation Trees.
Here is an example of how you can use grouping parameters to define a group of budgets for a security rule. Assume that you entered the following ChartField values in a security rule:
ChartField Combination Set#1:
|
ChartField |
Parameter |
Start |
End |
Tree |
Node |
|
ACCOUNT |
Wildcard |
501% |
-- |
-- |
-- |
|
DEPTID |
Range |
30000 |
32000 |
-- |
-- |
ChartField Combination Set#2:
|
ChartField |
Parameter |
Start |
End |
Tree |
Node |
|
ACCOUNT |
Tree |
-- |
-- |
BUD_ACCOUNT |
682000 |
|
DEPTID |
Wildcard |
335% |
-- |
-- |
-- |
|
PRODUCT |
Range |
200 |
250 |
-- |
-- |
The following is an excerpt from the BUD_ACCOUNT ChartField tree for this example:
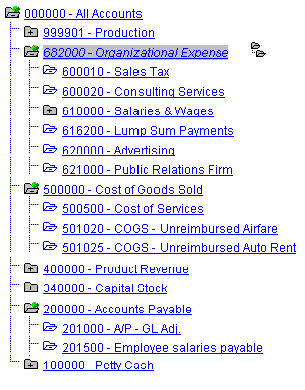
Accounts ChartField tree excerpt
Assume the following budgets are defined:
|
ACCOUNT |
DEPTID |
PRODUCT |
|
501020 |
20010 |
-- |
|
501020 |
30000 |
-- |
|
501025 |
30200 |
-- |
|
500500 |
31000 |
-- |
|
620000 |
35000 |
220 |
|
621000 |
33510 |
230 |
|
616200 |
33510 |
245 |
|
501020 |
33510 |
245 |
Your security rule would apply to the budgets whose ChartField values appear in italics in the table.
Conflicting Security Rules
If a budget action, or event, by a user passes any one rule, it passes the security check completely. The exception to this is when there are one or more rules that conflict. In a conflicting rules situation, the default is to disallow and the action fails security.
For example, if rule 1 is allow budget entry for Deptid 10000 through 20000 and rule 2 is to Disallow budget entry for Deptid 12000 through 21000 and both rules are assigned to the same user there is a conflict. Any attempt by that user to do a budget entry for Deptid 12000 through 20000 fails Commitment Control security.
Dynamic Security Rules
You use dynamic rules to assign security events to a ChartField that you define as a bind variable rather than a particular value or range of values. The bind variable is resolved by a view, called the dynamic rule record, that associates a user ID with a ChartField value.
See the discussion of Attaching Rules to Dynamic Rule Groups in the section, Security Rule Assignment, below.

 Security Rule Assignment
Security Rule AssignmentOnce you have defined your security rules and applied those rules to events and business units, you are ready to attach the rules to users. You have the option to attach rules to single user IDs, to permission lists, or to dynamic rule groups.
Attaching Rules to User IDs
Assigning security rules to user IDs enables you to attach specific security rules to individuals. This can be tedious and can require a lot of maintenance for a large number of users, but it does provide a useful method for attaching special rules (such as a Super User rule) to select users.
Attaching Rules to Permission Lists
Often you need to assign the same budget security to all the users of a permission list. While you could assign the security rule to each individual user, this would produce a maintenance issue in that if you needed to add a new security rule, you would have to add this rule multiple times. By taking advantage of the permission lists set up as part of your standard PeopleSoft application security, you can attach rules to a permission list, which then enables these rules for all users associated with the permission list.
Attaching Rules to Dynamic Rule Groups
In cases where a user is associated with a particular ChartField value, such as a manager and a department ID, you can create dynamic security rules and dynamic rule groups. Dynamic rule groups use a SQL view that you must define yourself, called the dynamic rule record, that joins the user ID and the ChartField value. Each user in the dynamic rule group has access to the budgets that include the ChartFields that the user is associated with in the dynamic rule record, for the security events defined in the dynamic security rule. This is far more convenient than creating and maintaining separate rules and attaching them individually to each user.
To set up dynamic rule groups, do the following:
Define a dynamic security rule in the Rule Definitions component. This rule assigns a bind variable to the ChartField that is resolved by the dynamic rule record.
Use Application Designer to define a dynamic rule record, a SQL view that includes the user ID field and the ChartField that uses the parameter Bind in the dynamic rule. For an example of a dynamic rule record, see the delivered record KK_DYN1 by opening the record in the PeopleSoft Application Designer.
Define a dynamic rule group by attaching the dynamic security rule to the dynamic rule record on the Attach Dynamic Rules page.
The Commitment Control Security process (KK_SEC_FLAT) creates security rows using the user ID and ChartField values from the dynamic rule record rows.
Dynamic Rule Group Example
Assume you want to allow department managers to inquire only on their own departmental budgets. Do the following:
Define a dynamic security rule with department ID (DEPTID) defined as a bind variable and apply it to the Budget Inquire security event.
Define a dynamic rule record with the fields user ID (OPRID) and department ID, based on a join of the DEPT_TBL, the PERSONAL _DATA table, and the OPRALIAS table:
SELECT a.deptid , C.OPRID FROM PS_DEPT_TBL A , PS_PERSONAL_DATA B , PSOPRALIAS C WHERE A.MANAGER_NAME = B.NAME AND B.EMPLID = C.EMPLID
Define a dynamic rule group by attaching the dynamic security rule to the dynamic rule record.
Run the Commitment Control Security process.
See Also
Assigning Commitment Control Security Rules
 Setting Up Commitment Control Security Fields
Setting Up Commitment Control Security FieldsTo set up commitment control security fields, use the Field Setup component (KSEC_CHARTFIELD).
This section describes how to enable ChartFields for Commitment Control security.
See Also

 Page Used to Define Security Fields
Page Used to Define Security Fields
|
Page Name |
Object Name |
Navigation |
Usage |
|
KSEC_CHARTFIELD |
Commitment Control, Define Budget Security, Field Setup, Commitment Control Security Field Setup |
Define key ChartFields to be used when defining security rules in the Security Rules component, along with the prompt table for each key ChartField. These values are delivered by PeopleSoft. Do not make changes on this page unless you are doing a reconfiguration of your ChartFields. |

 Defining Security Fields
Defining Security Fields
Access the Commitment Control Security Field Setup page.
Warning! Do not edit the delivered security fields unless you are configuring your Commitment Control ChartFields.
|
Security Field |
Do not make changes to these fields unless you are changing your ChartField configuration from that delivered. If you make changes, you can select a field for which you want to enable security. Security can be enabled for any field that is a key ChartField for control budget definitions, including Budget Period, Ledger Group, and Ledger. |
|
Record Name (table name) |
Do not make changes to these fields unless you are changing the configuration of the delivered ChartFields. These values are the record, or table, names that the system prompts against when you specify field values for a ChartField on the Rule Definition page. Use the records defined in the Commitment Control ledger template as the RECNAME or the RECNAME_EFFDT. |
 Setting Up Commitment Control Security Events
Setting Up Commitment Control Security EventsTo set up commitment control security events, use the Events component (KSEC_EVENT_ENTRY).
This section describes how to activate security for specific Commitment Control functions, known as security events.
See Also

 Page Used to Activate Security Events
Page Used to Activate Security Events
|
Page Name |
Object Name |
Navigation |
Usage |
|
KSEC_EVENT_ENTRY |
Commitment Control, Define Budget Security, Events, Commitment Control Security Events |
Activate and inactivate security for specific Commitment Control functions, or events. |

 Activating Security Events
Activating Security Events
Access the Commitment Control Security Events page.
Check the check box for any of the seven security events (commitment control functions) to which you want to restrict access or add constraints to the use of the events.
 Setting Up Commitment Control Security Rules
Setting Up Commitment Control Security RulesTo set up commitment control security rules, use the Security Rule Definition component (KSEC_RULE_ENTRY).
Security rules enable you to establish, independently of any specific user, which security events can be performed on which budgets. Setup for security rules consists of two steps, described in this section:
Defining the security rules and applying them to business units.
Applying the security rules to security events.
See Also

 Pages Used to Define Security Rules
Pages Used to Define Security Rules
|
Page Name |
Object Name |
Navigation |
Usage |
|
KSEC_RULE_ENTRY |
Commitment Control, Define Budget Security, Rule Definitions, Rule Definition |
Specify the key ChartField values and business units that define the budgets included in a security rule. |
|
|
KSEC_RULE_APPLY_TO |
Commitment Control, Define Budget Security, Rule Definitions, Apply Rule |
Apply the attributes that you defined on the Rule Definition page to one or more security events. |

 Defining Security Rules
Defining Security Rules
Access the Rule Definition page.
|
Attribute |
Select one of the following:
|
|
Rule Type |
Select one of the following:
|
Security Rule Combination
|
Combination Set |
Each combination set represents a budget or range of budgets (depending on the parameters you use to select ChartField values). When you add a new combination set, the system generates a sequential combination set number. When more than one ChartField is being secured in combination with other ChartFields, establish combination sets for a rule as opposed to defining individual rules for each ChartField value or range of ChartField values. To control for multiple ChartFields that are interrelated, create a rule using multiple ChartField Combination Sets. For example if a user is to have access to the following ChartFields for these specific values:
Create the following ChartField Combination Sets for one rule:
|
Budget ChartField Values and Budget ChartField Tree Values
Apply Rule to Business Units
Apply the rule either to all valid business units or to the business units you specify in the grid.

 Applying Security Rules to Security Events
Applying Security Rules to Security EventsAccess the Apply Rule page.
Apply Rule to Security Events
|
Security Event |
Select the security events to which you want the security rule to apply:
OVERRIDE at the transaction level, or header level as for a complete override of a journal entry, can be done only by a Super User. However, overrides at the individual budget level do not have to be associated with a super user rule. BYPASS, and BUDG_DT are available only if you select Super User as an attribute on the Rule Definition page. Note. A security event need not be active for you to apply security rules to it, but the system only enforces security rules on active security events. |
See Security Events.
|
|
Click to see a discussion of why you should or should not include ledger group as a security field for this event. You enter security fields in the ChartField column on the Rule Definition page. |
Applicable Modules for Budget Date Event
Available only when you select the BUDG_DT(budget date override)Security Event.
|
All Modules |
Click to allow budget date override for all feeder application modules. |
|
Specify Modules |
Click to specify which feeder application modules allow budget date override. Enter selections in the Module field. |
Applicable Source Transactions for Override Event
Available only when you select the OVERRIDE(budget override)Security Event.
|
All Source Transactions |
Click to allow transaction override for all source transaction types. |
|
Specify Source Transactions |
Click to specify which source transaction types allow budget checking overrides. Enter selections in the Source Transaction Type fields. |
Note. Selecting Do not Allow Override as the Override Budget Checking option for a source transaction type on the Source Transactions - Options page is only effective if the override event is inactive within commitment control security.
 Assigning Commitment Control Security Rules
Assigning Commitment Control Security RulesTo assign commitment control security rules, use the following components:
Attach Rules to User ID (KSEC_OPR_RULES).
Attach Rules to Permission List (KSEC_CLSS_RULES).
Attach Dynamic Rules (KSEC_DYN_RULES).
Once you have defined your security rules, you must assign them to users. This section describes how to:
Assign security rules to a user ID.
Assign security rules to a permission list.
Assign dynamic rules to dynamic rule groups.
See Also
Setting Up Commitment Control Security Rules

 Pages Used to Assign Commitment Control Security Rules
Pages Used to Assign Commitment Control Security Rules
|
Page Name |
Object Name |
Navigation |
Usage |
|
KSEC_OPR_RULES |
Commitment Control, Define Budget Security, Assign Rule to User ID, Assign Commitment Control Security Rule to User ID |
Assign security rules to individual user IDs. You can attach multiple security rules to a user ID. |
|
|
KSEC_CLSS_RULES |
Commitment Control, Define Budget Security, Assign Rule to Permission List, Assign Commitment Control Security Rule to Permission List |
Assign security rules to permission lists. You can attach multiple security rules to a permission list. |
|
|
KSEC_DYN_RULES |
Commitment Control, Define Budget Security, Assign Rule to Dynamic Group, Assign Commitment Control Security Rule to Dynamic Group |
Assign security rules to dynamic rule groups. You can attach multiple security rules to a dynamic rule group. The security rules identify the ChartField values and thus the users for whom you are assigning security. |

 Attaching Rules to User IDs
Attaching Rules to User IDs
Access the Assign Commitment Control Security Rule to User ID page.
Select the security rules you want to assign to the user ID. You can assign only Regular rule types to user IDs. If the security rules you assign have conflicting Allow/Disallow attributes, the Disallow attribute takes precedence. For example, if security rule A allows inquiries on budgets with account 10000 and security rule B disallows inquiries on account 10000, security rule B takes precedence for account 10000.

 Attaching Rules to Permission List
Attaching Rules to Permission ListAccess the Assign Commitment Control Security Rule to Permission List page.
The same factors that apply to attaching rules to User IDs apply when you attach rules to permission lists.

 Attaching Dynamic Rules
Attaching Dynamic RulesTo attach dynamic security rules to a dynamic group:
Define a dynamic rule record for the security rule.
In Application Designer, create a view that includes:
User ID (OPRID).
The ChartField that uses the parameter bind in the dynamic security rule.
For an example, see the delivered sample dynamic record KK_DYN1, which includes department ID and user ID. This view was created with the following SQL:
SELECT a.deptid , C.OPRID FROM PS_DEPT_TBL A , PS_PERSONAL_DATA B , PSOPRALIAS C WHERE A.MANAGER_NAME = B.NAME AND B.EMPLID = C.EMPLID
Access the Assign Commitment Control Security Rule to Dynamic Group page by entering a dynamic rule group ID and the dynamic rule record.
Select the security rules you want to assign to the user ID.
You can assign only Dynamic rule types to dynamic rule groups, and only dynamic rules that define the ChartField on the dynamic rule record as a bind variable. If the security rules you assign have conflicting Allow/Disallow attributes, the Disallow attribute takes precedence. For example, if security rule A allows inquiries on budgets with account 10000 and security rule B disallows inquiries on account 10000, security rule B takes precedence for account 10000.
See Also
Enterprise PeopleTools 8.46 PeopleBook: PeopleSoft Application Designer
 Running the Commitment Control Security Application Engine Process (KSEC_FLAT) and the Commitment Control Security Report
(GLC8572)
Running the Commitment Control Security Application Engine Process (KSEC_FLAT) and the Commitment Control Security Report
(GLC8572)Before your security rules and assignments can take affect, you must run the Commitment Control Security Application Engine process (KSEC_FLAT) to create the tables used by the system to check security access. You can view the results of the process on the Commitment Control Security report (GLC8572).

 Pages Used to Run the Commitment Control Security Process
Pages Used to Run the Commitment Control Security Process
|
Page Name |
Object Name |
Navigation |
Usage |
|
KSEC_AE_RNCNTL |
Commitment Control, Define Budget Security, Request Build, Request Build Commitment Control Security |
Request a run of the Commitment Control Security Application Engine process (KSEC_FLAT). This process creates the security rules that are evaluated during transaction entry. No security rules are in effect until you run this process. Ensure that you activate security events that you wish to use prior to running this process. There are no request parameters required on this page. |
|
|
RUN_GLC8572 |
Commitment Control, Define Budget Security, Security Report, Commitment Control Budget Security Report |
Request a run of the Commitment Control Security Report (GLC8572). This Crystal report shows the security rules assigned to each User ID and permission list, along with details about the budgets and security events included in the security rules. There are no request parameters required on this page. |
See Also
Setting Up Commitment Control Security Rules
 Setting Up PS/nVision Reporting Security
Setting Up PS/nVision Reporting Security
Use the commitment control ledger template (COMMITMENT) to provide the option to access a secured reporting view for restricted commitment control ledger access for PS/nVision reports as discussed in the PeopleTools security documentation.
Specify the ledger reporting view LED_RPTG_KK_VW in the Secured Rptg Vw (secured reporting view) field to secure access to commitment control ledgers by authorized user IDs during PS/nVision reporting. Because this is an optional security field, if you do not specify a ledger reporting view, PS/nVision provides reporting directly against the ledger.

 Page Used to Set Up PS/nVision Reporting Security
Page Used to Set Up PS/nVision Reporting Security
|
Page Name |
Object Name |
Navigation |
Usage |
|
Templates - Record Definitions |
LEDGER_TEMPLATE1 |
General Ledger, Ledgers, Templates, Record Definitions |
Optionally specify a ledger reporting view in the Secured Rptg Vw (secured reporting view) field to enforce PS/nVision reporting security. |
See Also
Enterprise PeopleTools 8.46 PeopleBook: PS/nVision, Setting Up PS⁄nVision Security, Implementing PS/nVision Ledger-Based Data Security
Granting nVision Reporting Access