
 Understanding EPM Security
Understanding EPM SecurityThis chapter provides an overview of PeopleSoft security and discusses how to:
Establish Ascential DataStage security.
Specify system security options.
Establish setID and business unit security.
Secure dimensions and metrics.
Establish role and user based security.
Establish security bridges for your business intelligence tool.

 Understanding EPM Security
Understanding EPM SecurityThis section discusses:
PeopleSoft application security.
PeopleTools security.
EPM security.
EPM security setup.
Delivered EPM security views.

 PeopleSoft Application Security
PeopleSoft Application SecurityPeopleSoft applications use multilevel security to enable you to successfully manage shared data environments. You set up data access at different entry points within your system and define the most efficient path to data across business groups, tables, departments, pages, and so forth. You have full control over security definitions, selecting options to create a matrix that enables or restricts user access to data through a series of authorizations.
Security access covers three areas: networks, databases, and applications. Network security controls the overall point of entry into your system hardware and software resources. Database security narrows the scope of a user's information access. At the application level, security extends to the field level. This diagram illustrates PeopleSoft application security levels:
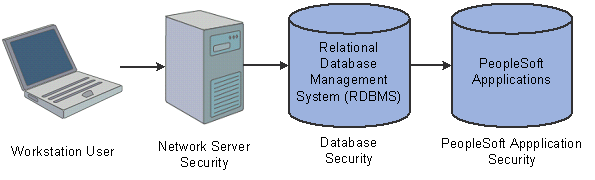
Levels of security in PeopleSoft applications
Application Security Terms
This table describes the various types of PeopleSoft application security:
|
Security Type |
Location |
Function |
|
Network |
Network software |
Controls entry into the network and authorizes rights to use shared resources. |
|
Relational Database Management System (RDBMS) |
Operating system |
Controls access to the database. |
|
User |
PeopleTools |
Controls access to application pages, functions, and business components. |
|
Object |
PeopleTools |
Controls access to objects or object groups that are used in application development. |
|
Query |
PeopleTools |
Defines table row sets that are accessed for performing system queries. |
|
Row-level |
PeopleTools and PeopleSoft applications |
Controls access to the subset of data rows within tables that the user is authorized to review or update. |
|
Field-level |
PeopleCode |
Controls access to individual fields on pages. |

 PeopleTools Security
PeopleTools SecurityPeopleTools security provides user authentication and application-level security. Users are authorized to access the EPM database using Peopletools login security. Users may be granted or denied access to each application and components therein. EPM security works together with PeopleTools security, so you must properly define PeopleTools security prior to setting up EPM security.
Prior to setting up PeopleSoft EPM row-level security:
Review your security needs and requirements.
Complete your PeopleTools role-level security setup.
See Enterprise PeopleTools PeopleBook: Security Administration

 EPM Security
EPM Security EPM security controls access to specific data within the EPM database. Specifically, it enables you to grant users access to specific rows, columns, or fields in an EPM database table. Data-access privileges within the warehouse can be defined for both Operational Warehouse - Enriched (OWE) and Multidimensional Warehouse (MDW) tables, and for dimension and fact tables.
You can specify security access using any of the following methods:
Field-level security: Enables you to set up field-level security for business units and setIDs. With field-level support, you can implement security to restrict users to specific fields on an EPM table because the tables are keyed by either setID or business unit.
Permission list security: Enables you to set up access privileges to groups of data by securing access to the business unit and setID fields based on a user permission list.
Dimension (row-level) security: Enables you to secure individual rows of an EPM table. With row-level support, you can implement security to restrict individual users or security roles to specific rows of data.
Metric-level security: Enables you to secure individual columns of an EPM table. Usually, these are measures on fact tables, but may also be attributes on a dimension table that contain sensitive data, such as Employees’ Salary or the Social Security Number columns. With metric-level support, you can implement security to restrict individual users or security roles to specific columns of data.
EPM security provides a single point of entry for defining and maintaining data access rules across all the EPM analytical applications and functional warehouses.

 Setting Up EPM Security
Setting Up EPM SecuritySetting up EPM security requires that you perform the following tasks:
Define PeopleTools role-based security.
Set up Ascential DataStage security.
Define system security options.
Specify security view names.
Apply security parameters for security options.
Define business unit and setID security parameters.
Designate dimensions and metrics to secure.
Assign users to metrics and dimensions.
Assign roles to metrics and dimensions.
Process security parameters for role and user security.
Refer to your application-specific PeopleBook for any special security setup that is required for an application.
See Also
Enterprise PeopleTools PeopleBook 8.46: Security Administration

 Delivered EPM Security Views
Delivered EPM Security ViewsPeopleSoft delivers security views for most of the securable objects in PeopleSoft EPM. To use these security views in PeopleTools, use the views as a search view.
|
Object |
Delivered EPM Security View |
|
Personal Data |
PERSONAL_SRCH |
|
Job Data |
JOB_SRCH |
|
Job Code |
JOBCODE_SRCH |
|
Product |
PRODUCT_SRCH |
|
Customer |
CUSTOMER_SRCH |
|
Channel |
CHANNEL_SRCH |
|
KPI (Key Performance Indicator) |
KPI_SRCH |
|
Location |
LOCATION_SRCH |
|
Model |
MODEL_SRCH |
|
Scenario |
SCENARIO_SRCH |

 Establishing Ascential DataStage Security
Establishing Ascential DataStage SecurityPeopleSoft EPM delivers the Ascential DataStage extract, transform, and load (ETL) tool to load data into the Operational Warehouse - Staging (OWS) layer of the warehouse and migrate the data to the Operational Warehouse - Enriched (OWE) and the Multidimensional Warehouse (MDW). The tool builds three layers of security into the repository and its objects. Access is granted through groups and users.
The three layers of security are:
A user role that is created by the EPM Production Manager.
The Production Manager assigns Windows user groups to one of four DataStage user categories. For example, if you belong to the Windows Administrators user group, you might be assigned to the DataStage Production Manager category and have full access to all areas of a DataStage project. This is the default for DataStage users.
Project privileges that range from browse-only to full Production Manager privileges.
Object-level safeguards that prevent users from jointly accessing or overwriting the same object.
For example, if a user is working on a job, that object is locked so that no other user can access it. Locks are automatically created to avoid repository contamination.
The following DataStage user categories are defined in PeopleSoft EPM: the EPM Production Manager, Developer, Operator, and None. The Production Manager has full access to all areas of a DataStage project, including repository objects, and can create and manipulate protected projects. The Production Manager grants access to all other groups and users. Developers have full access to all areas of a DataStage project and can create and modify ETL jobs. This is the default setting. Operators have permission to run and manage DataStage jobs. Users who are assigned to None do not have permission to sign in to DataStage.
See Also
Ascential DataStage Administrator's Guide

 Specifying System Security Options
Specifying System Security OptionsYou can set up field-level security for business units and setIDs. Because the data warehouse tables are keyed by either setID or business unit, you can control users or user groups access by business unit and setID.
The Security Options page enables you to apply this type of security. The page updates one row in the INSTALLATION_FS table. Only one row is ever in this table (only one type of security can be active at a time). For example, if you select operator security, only selected fields (business unit, setID, or both) have security applied.
This section discusses how to:
Set up field-level security options.
Set up security view names.

 Pages Used to Specify System Security Options
Pages Used to Specify System Security Options
|
Page Name |
Object Name |
Navigation |
Usage |
|
Security Options |
SECURITY_OPTIONS |
EPM Foundation, EPM Security, Advanced, Security Options |
Set up field-level security for business units and setIDs. |
|
Security View Names |
SECURITY_VIEWS |
EPM Foundation, EPM Security, Advanced, Security View Names |
Set up security view names. |
|
Request Security Processing |
RUN_FIN9001 |
EPM Foundation, EPM Security, Advanced, Apply Security Setups, Request Security Processing |
Run the Apply Security process to apply the security setup throughout the system. |

 Setting Up Field-Level Security Options
Setting Up Field-Level Security OptionsAccess the Security Options page.
You can implement security using either of the following fields:
|
Unit |
Business unit, the primary key for all transaction data. |
|
SetID |
The primary key for all accounting structure and rules tables. |
For either field, you can set the security in the following ways:
|
No Security |
Disables PeopleSoft application security. All users who are authorized to access a page may select any valid setID or business unit. |
|
Operator Level Security |
Enables PeopleSoft application security. Users are limited to the setIDs and business units that are specified by their user IDs. |
|
Permission List Level Security |
Enables PeopleSoft application security. Users are limited to the key fields that are specified by the permission list that is assigned to their user IDs. All users in a permission list have the same level of security. |

 Setting Up Security View Names
Setting Up Security View NamesAccess the Security View Names page.
Note. PeopleSoft EPM includes predefined security view names that tell the system which table views to reference. Views are SQL SELECT statements that filter out data rows whose key values are not needed as valid access parameters. The result is that users who are authorized to access setIDs or business units see only a subset of values from these edit table values. After you have set up these views, you can specify which users or permission lists can access the pages that contain secured field values. Within each page, you also can hide specific fields from particular permission lists.
The Security View Names page also tells you what type of field (business unit or setID) is secured by each view. The system stores the list in the SEC_VIEW_NAMES table, where you can review or update this information. You can add any security views that you configure for your system. PeopleSoft EPM is delivered with security views that apply to key fields in your system. You can alter these views or build views of your own. View names use one of three file extensions to reflect the type of security that you selected when you specified your security options:
_NONVW: Indicates that no security has been selected for that view.
_OPRVW: Indicates that operator (user) security has been selected for that view.
_CLSVW: Indicates that permission list security has been selected for that view.
|
Search Text |
Lists the view name prefixes that are supplied by each of your applications. When you run the Apply Security Setup process, the process uses this column to search the system for view names that begin with these prefixes. If a view name begins with a prefix from this list, the process changes the view name extension to match the security type that you selected when you specified security options. The type of field (business unit or setID) that is secured by each view is embedded in the view name. |
After you have selected your security options and defined your security views, you must run the Apply Security FIN9001 SQR process for the options to take effect.
See Also

 Running the Apply Security Process
Running the Apply Security ProcessAccess the Request Security Processing page.
Run the Apply Security process to apply the security parameters you set up on the Security Options and Security View Names pages. The Apply Security SQR process reads the INSTALLATION_FS table to determine the security type (none, permission list, operator) and then switches the prompt table views to the new view names, based on SEC_VIEW_NAMES. The process searches for the values in the Search Text field on the Security View Names page and replaces the table names as specified.
Note. This process should not be confused with the request security processing process (PF_SECURITY) which is discussed later in this chapter. The PF_SECURITY process applies security parameters specified for security roles and users.

 Establishing SetID and Business Unit Security
Establishing SetID and Business Unit SecurityAfter applying security, you need to determine which users have access to groups of data by securing access to the business unit and setID fields. For a specified business unit, you can determine which setIDs a user can work with. You do this either by permission list or user, depending on how you have established your PeopleTools role-based security.
This section discusses how to:
Establish setID security by permission list or user ID.
Establish business unit security by permission list or user ID.

 Pages Used to Establish SetID and Business Unit Security
Pages Used to Establish SetID and Business Unit Security
|
Page Name |
Object Name |
Navigation |
Usage |
|
TableSet Security by Permission List |
SEC_SETID_CLS |
EPM Foundation, EPM Security, Advanced, TableSet Security by Perm (Permission) List |
Establish setID security by permission list. Valid values for permission list are taken from your PeopleTools security setup. |
|
TableSet Security by User ID |
SEC_SETID_OPR |
EPM Foundation, EPM Security, Advanced, TableSet Security by User ID |
Establish setID security by user ID. Valid values for user are taken from your PeopleTools security setup. |
|
Unit Security by Permission List |
SEC_BU_CLS |
EPM Foundation, EPM Security, Advanced, Unit Security by Perm (Permission) List |
Establish business unit security by permission list. |
|
Unit Security by User ID |
SEC_BU_OPR |
EPM Foundation, EPM Security, Advanced, Unit Security by User ID |
Establish business unit security by user ID. |

 Establishing SetID Security by Permission List or User ID
Establishing SetID Security by Permission List or User IDAccess the TableSet Security by Permission List page or the TableSet Security by User ID page.
For each user ID or primary permission list, select the setID or setIDs that the users or permission list can access.

 Establishing Business Unit Security by Permission List or User ID
Establishing Business Unit Security by Permission List or User IDAccess the Unit Security by Permission List page or the Unit Security by User ID page.
For each user ID or primary permission list, select the warehouse business unit or units that the user or permission list can access.

 Establishing Ledger Security
Establishing Ledger Security
After specifying business unit and setID security, you need to determine which users have access to ledger data by securing access to specific ledgers. For a specified ledger you can grant access to users by permission list or user ID.

 Pages Used to Define Ledger Security
Pages Used to Define Ledger Security
|
Page Name |
Object Name |
Navigation |
Usage |
|
Ledger/Perm List |
SEC_LEDGER_CLS |
EPM Foundation, EPM Security, Advanced, Ledger Security by Permission List, Ledger/Perm List |
Select a ledger to associate with a security permission list. |
|
Ledger by User ID |
SEC_LEDGER_OPR |
EPM Foundation, EPM Security, Advanced, Ledger Security by User ID, Ledger by User ID |
Select a ledger to associate with a user ID. |

 Defining Ledger Security by Permission List or User ID
Defining Ledger Security by Permission List or User ID
Access the Ledger/Perm List or Ledger by User ID page.
Use these pages to select a ledger to associate with a security permission list or user ID.

 Securing Dimensions and Metrics
Securing Dimensions and MetricsBecause EPM is delivered with no security restrictions, dimensions and metrics (also known as fact-columns) are also delivered unsecured. Before you can grant a user access to a dimension or metric, you must first indicate to the system that a particular dimension or metric requires securing. The pages used to define dimension and metric security are discussed in the setups chapter of this PeopleBook.
See Setting Up EPM Foundation.
Note. Dimensions and metrics that are not secured are classified as public, or unsecured. All EPM users can view public objects.

 Pages Used to Secure Dimensions and Metrics
Pages Used to Secure Dimensions and Metrics
|
Page Name |
Object Name |
Navigation |
Usage |
|
Dimension |
PF_DIM_DEFN |
EPM Foundation, EPM Security, Metrics and Dimensions, Create/Edit Secured Dimension, Dimension |
Define and secure dimensions. This page is discussed in the “Setting Up and Working with EPM Foundation metadata” chapter. |
|
Define Metric |
PF_SY_METR_DEFN |
EPM Foundation, EPM Security, Metrics and Dimensions, Create/Edit Secured Metrics, Define Metric |
Define and secure metrics. This page is discussed in the “Setting Up and Working with EPM Foundation metadata” chapter. |

 Establishing Role and User Based Security
Establishing Role and User Based SecurityThis section provides an overview of role and user-based security and discusses how to:
Define security roles.
Grant dimension and metric access to security roles.
Assign users to security roles.
View summary for security roles.
Grant dimension and metric access to a user.
View summary for a secured user.
Request security processing

 Understanding Role and User-Based Security
Understanding Role and User-Based SecurityAfter you designate dimensions and metrics that require securing, you must grant users access to those objects. You can grant security access to an individual user or to a specific security role.
EPM security enables you to create security roles. A security role is a set of data access privileges that are assigned to one or more users. A user who is assigned to a specific role inherits all access privileges that are associated with that role. A user can belong to multiple roles. In this case, the user would inherit the combined privileges that are defined for all roles.
To set up security roles, define the role, assign dimension and metric access privileges to the role, and then assign users to the role. The following diagram depicts this process.
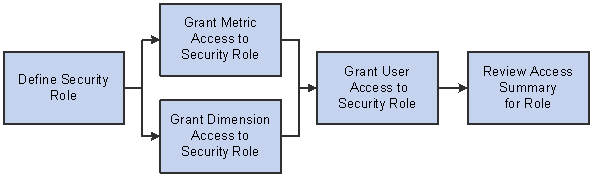
Process flow - security role setup
If you have established security roles for your PeopleTools security, you can import the roles into the EPM database using the Run Security Processing page.
See Processing Your Security Parameters.
EPM security also enables you to define access privileges for individual users. To set up user access privileges, assign dimension and metric access privileges to a specific user.
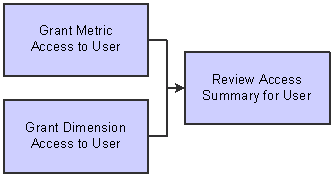
Process flow - user security setup
Dimension Security and Individual, Constraint, and Tree Based Selections
EPM security provides three methods to specify row-level security for your dimension:
Individual-based definition: Enables you to specify row-level security using the setID and dimension key fields.
Constraint-based definition: Enables you to specify row-level security by associating a constraint with a dimension table.
The constraint limits access to a dimension by acting as the WHERE clause in a SQL statement—for example, SELECT Account ID FROM Account Dimension WHERE Account ID = Northwest.
Set ID and Constraint ID are used to specify constraint access.
Tree-based definition: Enables you to specify row-level security using existing tree hierarchies that are defined for a dimension.
You can use the tree to grant a user access to specific nodes, leaves, or details in the tree. Tree hierarchy use is limited to OWE tables only.

 Pages Used to Establish Role and User-Based Security
Pages Used to Establish Role and User-Based Security
|
Page Name |
Object Name |
Navigation |
Usage |
|
Define EPM Security Roles |
PF_SY_ROLE_DEFN |
EPM Foundation, EPM Security, Security By Role, Define EPM Security Roles |
Define security roles. |
|
Access To Metric |
PF_SY_ROLE_METR |
EPM Foundation, EPM Security, Security By Role, Role Metric Access, Access To Metric |
Assign a metric to a security role. |
|
Role Dimension Access |
PF_SY_ROLE_ALL_MDW |
EPM Foundation, EPM Security, Security By Role, Role Dimension Access, Role Dimension Access |
Assign a dimension table to a security role and specify high-level access privileges. Note. The object name of this page changes depending on whether an OWE or MDW dimension is selected. |
|
Individual Selection |
PF_SY_ROLE_LIST |
EPM Foundation, EPM Security, Security By Role, Role Dimension Access, Individual Selection |
Specify row-level access to the dimension based on setID and dimension key fields. |
|
Constraint-based Selection |
PF_SY_ROLE_CONS |
EPM Foundation, EPM Security, Security By Role, Role Dimension Access, Constraint-based Selection |
Specify row-level access to the dimension based on constraint. |
|
Select Security Column |
PF_SY_COLUMN_PG |
Automatically accessed when you select a constraint on the Constraint-based Selection page that contains two or more columns and the system cannot distinguish the column you want to include in your security parameters |
Select one column to include in your constraint. |
|
Tree-based Selection |
PF_SY_ROLE_TREE |
EPM Foundation, EPM Security, Security By Role, Role Dimension Access, Tree-based Selection |
Specify row-level access to the dimension based on an existing tree hierarchy that is defined for the dimension. You can use the tree to grant a user access to specific nodes, leaves, or details in the tree. Used with OWE dimensions only. |
|
User Role Access |
PF_SY_USER_ROLES |
EPM Foundation, EPM Security, Security By User, User Role Access |
Assign a user to a security role. |
|
Role Security Summary |
PF_SY_ROL_SUMMARY |
EPM Foundation, EPM Security, Security By Role, Role Security Summary |
Review access privileges and other information for a security role. |
|
Review Role Dimension Access |
PF_SY_ROLE_DETAIL |
Click the Details link on the Role Security Summary page. |
Review additional details about a dimension that is associated with the selected security role |
|
Access To Metric |
PF_SY_ROLE_METR |
EPM Foundation, EPM Security, Security By User, User Metric Access, Access To Metric |
Assign a metric to a user. |
|
User Dimension Access |
PF_SY_ROLE_ALL |
EPM Foundation, EPM Security, Security By User, User Dimension Access, User Dimension Access |
Assign a dimension table to a user and specify high-level access privileges. |
|
Individual Selection |
PF_SY_ROLE_LIST |
EPM Foundation, EPM Security, Security By User, User Dimension Access, Individual Selection |
Specify row-level access to the dimension based on setID and dimension key fields. |
|
Constraint-based Selection |
PF_SY_ROLE_CONS |
EPM Foundation, EPM Security, Security By User, User Dimension Access, Constraint-based Selection |
Specify row-level access to the dimension based on constraint. |
|
Select Security Column |
PF_SY_COLUMN_PG |
Automatically accessed when you select a constraint on the Constraint-based Selection page that contains two or more columns and the system cannot distinguish the column you want to include in your security parameters. |
Select one column to include in your constraint. |
|
Tree-based Selection |
PF_SY_ROLE_TREE |
EPM Foundation, EPM Security, Security By User, User Dimension Access, Tree-based Selection |
Specify row-level access to the dimension based on an existing tree hierarchy that is defined for the dimension. You can use the tree to grant a user access to specific nodes, leaves, or details in the tree. Used with OWE dimensions only. |
|
User Security Summary |
PF_SY_SUMMARY |
EPM Foundation, EPM Security, Security By User, User Security Summary |
Review access privileges and other information for a user. |
|
Review User Dimension Access |
PF_SY_USER_DETAIL |
Click the Details link on the User Security Summary page. |
Review additional details about a dimension that is associated with the selected user. |
|
Request Security Processing |
RUN_PF_SECURITY |
EPM Foundation, EPM Security, Advanced, Request Security Processing |
Apply security parameters for security roles and users by running the request security processing (PF_SECURITY) process. |

 Defining Security Roles
Defining Security RolesAccess the Define EPM Security Roles page.
|
EPM Security Role |
Displays the name of the security role that you are defining. |
|
Role Type |
Displays the type of role that is being defined. Possible role types include EPM Role, System Role, User Role, WFA Generated Role. |
Users in This EPM Security Role
|
User ID |
Displays the users who are associated with this role. |

 Granting Metric Access to a Security Role
Granting Metric Access to a Security RoleAccess the Access To Metric page.
|
Metric ID |
Displays the metric that you are associating with a particular security role. |
|
Record Name |
Displays the record that is associated with the selected metric. |
|
Column Name |
Displays the column that is associated with the selected metric. |

 Granting Dimension Access to a Security Role
Granting Dimension Access to a Security RoleAccess the Role Dimension Access page.
|
Dimension |
Displays the dimension that you are associating with a particular security role. |
|
Warehouse |
Displays the warehouse layer that is associated with the selected dimension. |
Type of Access
|
Grant All |
Select this option to grant the role access to the entire dimension. |
|
No Access |
Select this option to bar the role from accessing the entire dimension. |
|
Selective Access |
Select this option to grant the role access to specific rows in the dimension. You can specify rows individually based on setIDs, using a constraint or using a hierarchy tree that is defined for the dimension (tree hierarchies are available only for OWE dimensions) . |

 Granting Individual Row-Level Access to a Role
Granting Individual Row-Level Access to a Role
Access the Individual Selection page.
|
Dimension |
Displays the dimension that you are associating with a particular security role. |
|
Warehouse |
Displays the warehouse layer that is associated with the selected dimension. |
Dimension Values
|
SetID or Business Unit |
Enter the setID or business unit that is associated with the dimension rows that you want to secure. This field can display either SetID or Business Unit, depending on the dimension you select. In some instances, there is no value displayed for the field . |
|
Dimension Key |
Enter the dimension key that is associated with the dimension. Because this is a dimension key field, the name of this field changes depending on the selected dimension. For example, if the Product (PRODUCT) table were selected, Product IDwould be displayed because it is the dimension key for that table. |

 Granting Constraint-Based Row-Level Access to a Role
Granting Constraint-Based Row-Level Access to a RoleAccess the Constraint-based Selection page.
|
Dimension |
Displays the dimension that you are associating with a particular security role. |
|
Warehouse |
Displays the warehouse layer that is associated with the selected dimension. |
Constraint-based Selection
|
SetID |
Enter the setID that is associated with the dimension rows that you want to secure. |
|
Constraint Code |
Enter the constraint that you want to associate with the selected dimension rows. You must have a constraint defined before you can access it here. If you do not have a constraint defined, you can use the Create Constraint link to create a new constraint. Note. The Select Security Column page displays if the constraint you select contains two or more columns and the system cannot distinguish the column you want to include in your security parameters. |
|
Reload |
Click to refresh the constraint definition if you have changed it after it was included in a security role. |
|
Security Column |
Displays the field from the constraint that is used as the column to restrict access. |
|
Create Constraint |
Click to access the Constraints page and define a constraint. If you have not created a constraint for the selected dimension rows, you can do so in the Constraints page. |

 Specifying Constraint Columns for Constraint-Based Row-Level Access
Specifying Constraint Columns for Constraint-Based Row-Level AccessAccess the Select Security Column page.
When you select a constraint (on the Constraint-based Selection page) that contains two or more columns and the system cannot distinguish the column you want to include in your security parameters, the Select Security Column page is accessed automatically. The page displays the columns available to use in the constraint you selected. You must choose just one of the columns for the constraint. Select the column you want to include by clicking the column name in the Key ID field.

 Granting Tree-Based Row-Level Access to a Role (OWE Dimension Only)
Granting Tree-Based Row-Level Access to a Role (OWE Dimension Only)Access the Tree-based Selection page.
|
Dimension |
Displays the dimension that you are associating with a particular security role. |
|
Warehouse |
Displays the warehouse layer that is associated with the selected dimension. |
Select Tree Values
|
SetID |
Enter the setID that is associated with the dimension rows that you want to secure. |
|
Tree ID |
Enter the hierarchy tree that you want to use to specify the dimension rows. |
|
Selection |
Displays the selected tree node value. |
|
|
Click the Find Selected Value button to display the selected node at the top of the hierarchy tree and make it easier for you to locate the node with which you are working. |
|
Parent Node |
Displays the parent node of the selected node. This field is blank if the selected node is a root node. |
|
Node Type |
Displays the node type of the selected node. Values can be Node or Detail. |
|
Selection Type |
Specify the level of detail to include with the selected node. Different values are available for your selection, depending on whether you have selected a node or a leaf from the hierarchy tree. If a node is selected, you can specify This Node Only, Immediate Children, Node and Immediate Children, All Descendants, or Node + All Descendants. If a leaf is selected, you can specify Immediate Child Leaves or All Descendant Leaves. If the leaf has a range of values, you must select Immediate Child Leaves. Trees with duplicate leaves are not supported. |
|
|
Click to add the selected node to the selection list. You must add a node to the selection list before the fields in the Selected Nodes and Leaves group box displays node values. |
|
Display Tree |
Click to display the hierarchy tree. |

 Assigning Users to a Security Role
Assigning Users to a Security RoleAccess the User Role Access page.
|
User ID |
Displays the user for whom you are granting role access. |
|
EPM Security Role Name |
Enter the security role that you want to associate with the selected user. |

 Viewing Security Summary for a Security Role
Viewing Security Summary for a Security RoleAccess the Role Security Summary page.
|
EPM Security Role Name |
Enter the security role for which you want to see a summary of access privileges. |
|
Display Summary |
Click to display the security role details and refresh the view. |
Dimension
|
Dimension Name |
Displays the dimensions that are associated with the selected security role. |
|
Warehouse |
Displays the warehouse layer that is associated with the selected dimension. |
|
Edit Access |
Click to access the Role Dimension Access page and edit the security role's access to the dimension. |
|
Details |
Click to access the Review Role Dimension Access page and examine additional details about the secured dimension, such as the setID or dimensionID. |
|
Add Dimension Access |
Click to access the Role Dimension Access page and grant the selected security role access to another dimension. |
Metrics
Click the Edit Metric Access link to access the Role Metric Access page and edit the security role's access to a metric.

 Review Role Dimension Access Summary
Review Role Dimension Access SummaryAccess the Review Role Dimension Access page.
Use this page to review additional details about your dimension that is associated with a particular security role.

 Granting Metric Access to a User
Granting Metric Access to a UserAccess the Access to Metric page.
The fields on this page are identical to the fields on the Access to Metric page for security roles. The only difference is that the fields on this page represent individual user access privileges and not a security role.

 Granting Dimension Access to a User
Granting Dimension Access to a UserAccess the User Dimension Access page.
The fields on this page are identical to the fields on the Role Dimension Access page. The only difference is that the fields on this page represent individual user access privileges and not a security role.

 Granting Individual Row-Level Access to a User
Granting Individual Row-Level Access to a UserAccess the Individual Selection page.
The fields on this page are identical to the fields on the Individual Selection page for security roles. The only difference is that the fields on this page represent individual user access privileges and not a security role.

 Granting Constraint-Based Row-Level Access to a User
Granting Constraint-Based Row-Level Access to a UserAccess the Constraint-based Selection page.
The fields on this page are identical to the fields on the Constraint-based Selection page for security roles. The only difference is that the fields on this page represent individual user access privileges and not a security role.

 Granting Tree-Based Row-Level Access to a User (OWE Dimension Only)
Granting Tree-Based Row-Level Access to a User (OWE Dimension Only)Access the Tree-based Selection page.
The fields on this page are identical to the fields on the Tree-based Selection page for security roles. The only difference is that the fields on this page represent individual user access privileges and not a security role.

 Viewing Security Summary for a User
Viewing Security Summary for a UserAccess the User Security Summary page.
|
User ID |
Enter the user for which you want to see a summary of access privileges. |
|
Display Summary |
Click to display security details for the user and refresh the view. |
Dimension
|
Dimension Name |
Displays the dimensions that are associated with the selected user. |
|
Warehouse |
Displays the warehouse layer that is associated with the selected dimension. |
|
Edit Access |
Click to access the User Dimension Access page and edit the user's access privileges to the dimension. |
|
Details |
Click to access the Review User Dimension Access page and examine additional details about the secured dimension, such as the setID or dimensionID. |
|
Add Dimension Access |
Click to access the User Dimension Access page and grant the selected user access to another dimension. |
Metrics
Click the Edit Metric Access link to access the User Metric Access page and edit the user's access to a metric.
Roles
|
EPM Security Role Name |
Displays the security roles that are associated with selected user. |
|
Edit Role Assignments |
Click to access the User Role Access page and edit the user's privileges that are associated with the role. |

 Review User Dimension or User Metric Access Summary
Review User Dimension or User Metric Access SummaryAccess the Review User Dimension Access page.
The fields on this page are identical to the fields on the Review Role Dimension Access page. The only difference is that the fields on this page represent individual user access privileges and not a security role.

 Processing Your Security Parameters
Processing Your Security ParametersAccess the Request Security Processing page.
|
EPM Role |
Enter the EPM security role that you want to process. If you leave this field blank, all security roles are processed. Note. You cannot process a security role and a user at the same time. |
|
User ID |
Enter the user you want to process. If you leave this field blank, all users are processed. Note. You cannot process a security role and a user at the same time. |
|
Dimension |
Enter the dimension that you want to process. If you leave this field blank, all dimensions are processed. |
|
Warehouse |
Enter the warehouse structure that is associated with the dimension you select for processing. |
|
Business Unit |
Enter the business unit that you want to process. Business unit is used to determine which record suite is used for the security job. |
|
Rerun Option |
Select this check box to rerun the security parameters process. |
Copy System Role to EPM
|
Rebuild Security Only |
Select this option if you want only to rebuild the security join tables. |
|
Copy Roles, Rebuild Security |
Select this option if you want to rebuild the security join tables and import PeopleTools security roles into the EPM database. |
|
Copy Roles Only |
Select this option if you want only to import PeopleTools security roles into the EPM database. |

 Establishing Security Bridges for Your Business Intelligence Tool
Establishing Security Bridges for Your Business Intelligence ToolThis section provides and overview of security bridges and discusses PeopleSoft delivered Application Programming Interfaces (APIs).

 Understanding Security Bridges
Understanding Security BridgesSecurity bridges provide a means to transfer EPM security profiles to your Business Intelligence (BI) database. This enables you to define your security parameters once in EPM without having to redefine them in your BI reporting tool.
Security bridges use Application Programming Interfaces (APIs) to transfer security profiles. APIs use programming commands to interface and communicate with your BI database and transfer EPM security profiles. A set of APIs is required to read data from EPM tables and another set is required to write data to your BI tables.
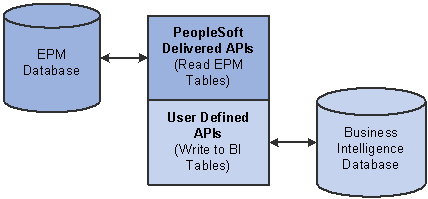
Security bridge and APIs
PeopleSoft prepackages APIs that are designed to read data from your EPM tables. However, you must create the code that writes data to your BI tables. PeopleSoft APIs are coded in Java and can function with any BI reporting tool.
PeopleSoft delivers the following APIs.

 Role Collection
Role CollectionThis class is a collection class of individual Role classes. The collection will inherit the normal Java methods to traverse the collection, for example, next(), first() etc. Also methods such as add(), remove() can be used and implemented as an ArrayList.
Public Methods
|
Name |
RoleCollection(JDBCConnection dbCon) |
|
Returns |
Nothing |
|
Parameters |
JDBCConnection dbCon. A valid JDBC Connection. |
|
Description |
This is the constructor used to instantiate the Role collection. |
|
Name |
LoadAllRoles() |
|
Returns |
Nothing |
|
Parameters |
None |
|
Description |
This method clears out the current elements in the collection and load it with all the currently defined Roles in EPM. |

 Role
RoleThis class defines a single Role defined in the EPM row-level security framework.
Public Methods
|
Name |
Role(JDBCConnection dbCon, String Name); |
|
Returns |
Nothing |
|
Parameters |
JDBCConnection dbCon. A valid JDBC Connection. |
|
Description |
The constructor for the Role class. Takes JDBC Connection and RoleName as parameters. Given a rolename, the constructor will fill up the other properties such as Type and Description. Note. There is no public constructor of the format Role(), you cannot instantiate this class without a name. |
|
Name |
getUsers(); |
|
Returns |
List of UserNames |
|
Parameters |
None |
|
Description |
The method will return a List of User Names that belong to this Role. A standard Java List object can be used to implement this. |
|
Name |
getAccessibleDimensions(); |
|
Returns |
List of Dimension Names |
|
Parameters |
None |
|
Description |
The method will return a List Dimension names that this Role can access. |
|
Name |
hasAccess (String DimName); |
|
Returns |
integer 0 or 1 |
|
Parameters |
Dimension Name |
|
Description |
The method returns a Boolean specifying whether the Dimension referenced by DimensionName parameter is available to the Role or not. |
|
Name |
hasAccess(String DimName, int DimValue); |
|
Returns |
integer 0 or 1 |
|
Parameters |
Dimension Name, A surrogate key value |
|
Description |
The method returns 0 or 1 specifying whether this Role has access to a particular value in a dimension. |
|
Name |
hasAllAccess(String DimName); |
|
Returns |
integer 0 or 1 |
|
Parameters |
Dimension Name |
|
Description |
The method returns a Boolean specifying whether this Role has ALL access to the Dimension referenced by DimensionName parameter. |
|
Name |
getDimensionValues(String DimName); |
|
Returns |
List of Values |
|
Parameters |
Dimension Name |
|
Description |
The method returns a List of values in the Dimension referenced by DimName that are available to the Role. The method will first check to ensure that the Dimension Name is a valid Secured dimension in the system, and it is accessible to the Role. The method will retun a List of values from the appropriate security join table. If the Role has ALL access to this dimension, the List will contain only one value with the pre-determined surrogate key value for ALL. Will return an empty List if the dimension is not available to the Role. |
|
Name |
getName(); |
|
Returns |
String Name |
|
Parameters |
None |
|
Description |
Get method for Name |
|
Name |
getType(); |
|
Returns |
String Name |
|
Parameters |
None |
|
Description |
Get method for Type |
|
Name |
getDescription(); |
|
Returns |
Stirng Descr |
|
Parameters |
None |
|
Description |
Get method for Description |
|
Name |
getLongDescription(); |
|
Returns |
String Description |
|
Parameters |
None |
|
Description |
Getter method for Long Description |

 User Collection
User CollectionThis class contains the same information as the Role Collection class. The only difference is that the values for this class represent user collection and not role collection.

 User
UserThis class contains information about a single User defined in EPM Security.
Public Methods
|
Name |
User(JDBCConnection dbCon, String Name); |
|
Returns |
Nothing |
|
Parameters |
JDBC Connection, String UserName |
|
Description |
The constructor for the User class. Takes Name as the one and only parameter. |
|
Name |
getRoles(); |
|
Returns |
List of RoleNames |
|
Parameters |
None |
|
Description |
The method will instantiate a List of Role Names that contain this User. |
|
Name |
getAccessibleDimensions(); |
|
Returns |
List of Dimension Names |
|
Parameters |
None |
|
Description |
The method will return a List of Dimension names that this User can access. This will be a combined list of all dimensions that the user can access via all his roles. |
|
Name |
hasAccess (String DimName); getAccessibleMetrics() |
|
Returns |
integer 0 or 1 |
|
Parameters |
Dimension Name |
|
Description |
The method returns a Boolean specifying whether the Dimension referenced by DimensionName parameter is available to the User or not. This method queries all the Roles for this user to determine if the user has access to the dimension. |
|
Name |
hasAccess(String DimName, int DimValue); |
|
Returns |
integer 0 or 1 |
|
Parameters |
Dimension Name, A surrogate key value |
|
Description |
The method returns 0 or 1 specifying whether this User has access to a particular value in a dimension. This method queries all the Roles for this user to determine if the user has access to the dimension and value. |
|
Name |
hasAllAccess(String DimName); |
|
Returns |
integer 0 or 1 |
|
Parameters |
Dimension Name |
|
Description |
The method returns a Boolean specifying whether this User has ALL access to the Dimension referenced by DimensionName parameter. If any of the user’s Roles has ALL access, the user is deemed to have ALL access. |
|
Name |
getDimensionValues(String DimName); |
|
Returns |
List of Values |
|
Parameters |
Dimension Name |
|
Description |
The method returns a List of values in the Dimension referenced by DimName that are available to the User. The method first checks to ensure that the Dimension Name is a valid Secured dimension in the system, and it is accessible to the User. This is a combined list of values from all the user’s Roles. The method returns a List of values from the appropriate SJT. If the User has “all” access to this dimension, the List will contain only one value with the pre-determined surrogate key value for “all”. Will return an empty List if the dimension is not available to the User. |
|
Name |
getName(); |
|
Returns |
String Name |
|
Parameters |
None |
|
Description |
Get method for Name |

 Dimension Collection
Dimension CollectionThis class contains information about the list of dimensions defined as secured dimensions in EPM Security. Each element of the collection is a Dimension class that represents one secured Dimension in the EPM system. The collection will inherit the normal Java methods to traverse the collection, for example, next(), first() etc. Also methods such as add(), remove() can be used.
Public Methods
|
Name |
DimensionCollection(JDBCConenction dbCon) |
|
Returns |
Nothing |
|
Parameters |
JDBC Connection |
|
Description |
This is the constructor used to instantiate the Dimension collection. This class is derived from one of the Java Collection classes, possibly ArrayList, or LinkedList. Most of the methods needed are inherited from the Collection class. Next(), Previous(), HasNext(), size() etc. The constructor will instantiate an empty collection. |
|
Name |
LoadAllDimensions() |
|
Returns |
Nothing |
|
Parameters |
None |
|
Description |
This method will clear out the current elements in the collection and load it with all the currently secured dimensions in EPM. |

 Dimension
DimensionThis class contains information about a single Dimension defined in the EPM database.
Public Methods
|
Name |
Dimension (JDBC Connection, String Name) |
|
Returns |
String Name |
|
Parameters |
JDBC Connection |
|
Description |
This is the constructor for this class. Takes a Dimension Name as parameter. The constructor will validate that the dimension specified by Name is a valid secured dimension in EPM. If it is an invalid name, or the dimension is not secured, the constructor will fail. |
|
Name |
getRoles() |
|
Returns |
List of Role Names |
|
Parameters |
Nothing |
|
Description |
This method will return a list of all Role names that have access to this dimension. |
|
Name |
getUsers() |
|
Returns |
List of User Names |
|
Parameters |
Nothing |
|
Description |
This method will return a list of all User names that have access to this dimension. |
|
Name |
getDimName() |
|
Returns |
Stirng Name |
|
Parameters |
None |
|
Description |
Get method for Name. |
|
Name |
getDimTableName() |
|
Returns |
String TableName |
|
Parameters |
None |
|
Description |
Get method for Table Name. |
|
Name |
getDimKeyName() |
|
Returns |
String KeyName |
|
Parameters |
None |
|
Description |
Get method for Key Name. |
|
Name |
isSecured() |
|
Returns |
Boolean |
|
Parameters |
None |
|
Description |
Get method for isSecured. |

 MetricCollection
MetricCollectionThis class contains information about metric collection.
Public Methods
|
Name |
MetricCollection(JDBCConnection dbCon) |
|
Returns |
Nothing |
|
Parameters |
A valid JDBCConnection |
|
Description |
This is the constructor used to instantiate the Metric collection. The constructor will instantiate an empty collection. |
|
Name |
LoadAllMetrics() |
|
Returns |
Nothing |
|
Parameters |
None |
|
Description |
This method will clear out the current elements in the collection and load it with all the currently secured metrics in EPM. |

 Metric
MetricThis class contains information about the metrics (columns) setup in EPM Security. This is for the Column-level security.
Public Methods
|
Name |
Metric(JDBCConnection dbCon , String Name) |
|
Returns |
Nothing |
|
Parameters |
JDBCConnection dbCon , String Name |
|
Description |
This is the constructor for this class. Takes a Dimension Name as parameter. There is no other public constructor. You need at least a Dimension Name to instantiate this class. The constructor will validate that the dimension specified by Name is a valid secured dimension in EPM. If it is an invalid name, or the dimension is not secured, the constructor will fail. |
|
Name |
getColName() |
|
Returns |
String Column Name |
|
Parameters |
None. |
|
Description |
This method will return the column name that the metric defines. |
|
Name |
getRecName() |
|
Returns |
String Record Name |
|
Parameters |
None |
|
Description |
This method will return the Record name that the metric defines. |

 JDBCConnection
JDBCConnectionThis class is used to connect to a database using a JDBC driver.
Public Methods
|
Name |
makeConnection() |
|
Returns |
Nothing |
|
Parameters |
None |
|
Description |
This method will connect to a JDBC database. The parameters needed to connect will be read from jdbcconnection.property file. |
|
Name |
makeConnection(String theDriverName, String theDbURL) |
|
Returns |
Nothing |
|
Parameters |
Driver Name, DB URL string |
|
Description |
This method will connect to a JDBC database. The parameters needed to connect are passed into the method. |
|
Name |
makeConnection(String theDriverName, String theDbURL, String theUserName, String thePassword) |
|
Returns |
Nothing |
|
Parameters |
JDBC Driver Name to be used to attempt the connection, URL for database to connect, User Name, Password |
|
Description |
This method will connect to a JDBC database. The parameters needed to connect are passed into the method. |
|
Name |
closeConnection() |
|
Returns |
Nothing |
|
Parameters |
None |
|
Description |
This method will close the connection. |
|
Name |
getDbResultSet(String pTheQuery) |
|
Returns |
ResultSet |
|
Parameters |
Query sent to the database. |
|
Description |
This method will execute the query and return a ResultSet object. |