Setting Up Personal Number Security
The Personal Number Security works on top of the existing Row Level Security. Only the users with the new permission list HCCPHRMYNUMBER will have access to the Personal Number Security component.
The Super User uses this component to setup the security for the Personal Number. You can define the security either for a User ID or for a Role.
|
Page Name |
Definition Name |
Usage |
|---|---|---|
|
HR_PERSNO_SEC_JPN |
Define the security. |
Use the Set Up Personal Number Security (HR_PERSNO_SEC_JPN) page to define the security.
Navigation:
This example illustrates the fields and controls on the Set Up Personal Number Security page.
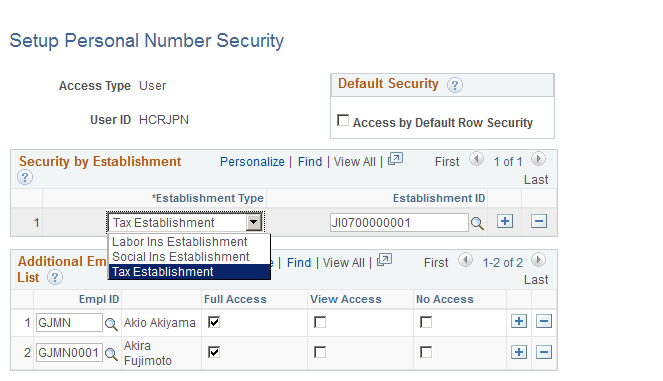
Field or Control |
Description |
|---|---|
Access by Default Row Security |
Select to enable default Row Level Security Access. The User or Role will have full access to the Personal Number of the Employees based on the existing Row Level Security. |
Establishment Type |
Select Establishment Types for a user or Role. The User/Role will have full access to the Personal Number of all the Employees who belong to the selected establishments. The list contains Labor Insurance Establishment, Social Insurance Establishment and Tax Establishment. |
Additional Employee List |
Select Employees whose Personal Number access needs to be overridden. The Access rights to an Employee's Personal Number can be overridden here. |
Full Access |
Select to define the edit access for a User/Role to his/her Personal Number. The user can update or delete the number. |
View Access |
Select to define the view access for a User/Role to his/ her Personal Number. The user cannot update or delete the number. |
No Access |
Mask the access of the Personal Number for a User/Role. |
Note: A user or Role will not have access to the Personal Number of an employee by default even if he/she has row level access to the Personal Data component. It is mandatory to add a row for the user or role on the above component if he or she needs access to the Personal Number.
Since a user can have multiple roles and each of these roles can have a row in the component, it is important to evaluate the Security setup. If an employee is given Full Access under Role 1 and if the same employee is given No Access under Role 2 and if user A has both Role 1 and Role 2 tagged to him or her, then No Access takes priority.