
 Understanding the Security Object Model
Understanding the Security Object ModelThis chapter provides an overview of the Security Object model and discusses how to define and maintain security.
See Also
Setting Up PeopleSoft Customer Relationship Management Security and User Preferences

 Understanding the Security Object Model
Understanding the Security Object ModelIn the financial services and insurance industries, every financial account and policy has a matrix of security rules. This security matrix contains information about an individual's reach and limit for a particular account. The Security Object model contains the matrix of security rules. When creating or maintaining an account, security keys are created.
The following diagram shows the process flow of the Security Object model.
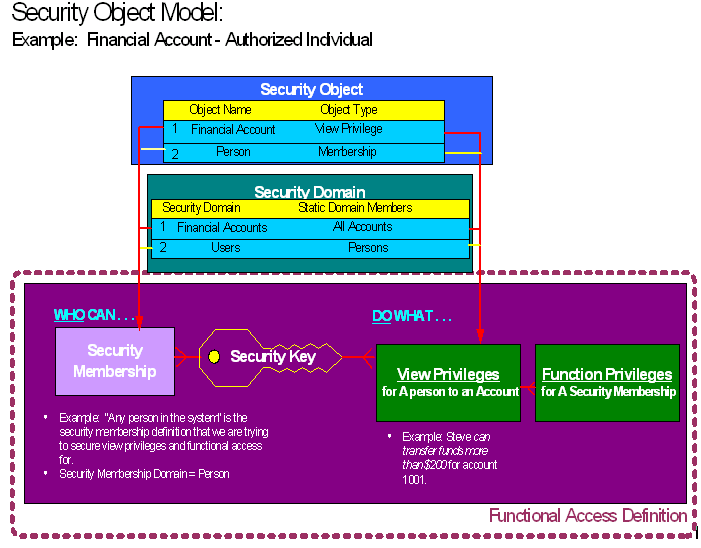
Security Object model
Security Objects
Security objects are delivered with the system. Any changes to the security objects affect security keys and the security list table. For this reason, PeopleSoft recommends limiting the number of security objects created. Two security objects are delivered. The Financial Account security object is a view privilege type security object, and the Authorized Users (ACCOUNTHOLDER) is a membership type security object. Both objects are system data. Not all objects can be used as security objects.
The security domain for the aforementioned security objects is a static list. The view object domain of the Financial Account object consists of all available accounts. Although these security domains are delivered and designed as static lists, you can define your own dynamic domains.
Security keys are created for each individual that takes part in the security model. One security key is generated for each individual. Security keys are created and maintained by either enterprise integration points, or by the online security matrix component.

 Defining and Maintaining Security
Defining and Maintaining SecurityThis section provides an overview of security definitions and maintenance, and discusses how to:
Maintain the security matrix.
Review access trace information.
Set up navigation security.

 Understanding Security Definition and Maintenance
Understanding Security Definition and Maintenance
The administrator uses the security matrix to define and maintain permissions granted to system users. Each row in the matrix represents a specific transaction for a specific account.
The security matrix can be populated using the Security Matrix page or programmatically.
Use the Security Matrix page to add, delete, or update rows in the security matrix.
Enterprise integration points are used to created financial accounts and their security. The inbound EIP receives the security matrix data, and the subscription code creates the security keys.
Each time an agent accesses a customer account through the 360-Degree View page, the security trace provides an audit trail.
The administrator uses navigation security to show or hide individual component items in the Agent view. Permission lists and roles determine portal navigation. Navigation security layers control access to specific menu items.

 Pages Used to Define and Maintain Security
Pages Used to Define and Maintain Security
|
Page Name |
Object Name |
Navigation |
Usage |
|
RSEC_SRTY_MAT_SRCH |
Set Up CRM, Security, Financial Services, Security Matrix |
Define permissions granted to system users. |
|
|
RBF_SRTY_TRC_SRCH |
Set Up CRM, Security, Financial Services, Access Trace, Security Trace Access |
View an audit trail of all user account access. |
|
|
RBF_NAV_SECURITY |
Set Up CRM, Security, Financial Services, Navigation Security |
Grant or remove access to content on the portal pages. Hide certain pages for a particular PeopleTools role even though role users have access to the components. |
|
|
RBF_ROLE_MAPPING |
Set Up CRM, Security, Financial Services, Role Mapping |
Map roles. |
|
|
RBF_SALES_VKEY |
Set Up CRM, Security, Financial Services, Sales Process Verification Key |
Validates employee status. |

 Maintaining the Security Matrix
Maintaining the Security Matrix
Access the Security Matrix page.
|
Account Number |
Select the applicable account number. You need one row for each allowable transaction on the account. You must have at least one row for each account; however, you may have multiple rows per account. |
|
Transaction Code |
Specifies the type of financial transaction for which the security is built. |
|
Approved |
Select to indicate that the transaction is allowed for this account. |
|
Conditional Operator |
Select if the transaction is allowed with a condition and populate operator applicable for the condition. |
|
Conditional Amount |
Select the amount for the condition. |
|
Message Catalog Set Number |
Displays the message catalog entry that a user sees when denied to perform a transaction due to insufficient security. |
Access the Security Matrix page: Audit Info tab (audit information).
The system displays an audit trail of all additions and modifications to the security matrix.

 Reviewing Access Trace Information
Reviewing Access Trace Information
Access the Security Trace Access page.
|
Start Date/Time |
Displays when the agent accessed the customer accounts through 360-Degree View page. |
|
End Date/Time |
Displays when the agent released the 360-Degree View page. Using the Back on the browser toolbar does not release the 360-Degree View page. The agent can still access the page by clicking Agent View or the forward button. If the agent signs out of the PeopleSoft application by clicking the Sign Out link or closing the browser, the closing timestamp not recorded. To release the 360-Degree View page and record the closing timestamp, click the Finish and Return to Search link on the 360-Degree View page. |

 Setting Up Navigation Security
Setting Up Navigation Security
Access the Navigation Security page.
|
Role Name |
PeopleTools role for which navigation security is applied. |
|
Portal Name |
Portal name in which the left navigation menu item is secured. |
|
Portal Label |
Label name of the left navigation menu for which security is applied. |

 Defining Role Mapping
Defining Role Mapping
Access the Role Mapping page.
|
System Role Name |
Lists the system-defined roles delivered. |
|
User - Defined Role Name |
Lists the customer's roles that will be mapped to the system-defined roles. |

 Defining Sales Process Verification Keys
Defining Sales Process Verification Keys
Access the Sales Process Verification Key page.
|
Verification Key |
Used in the sales process to verify employment of employees and existence of company contract. |
See Also
Setting Up PeopleSoft Customer Relationship Management Security and User Preferences